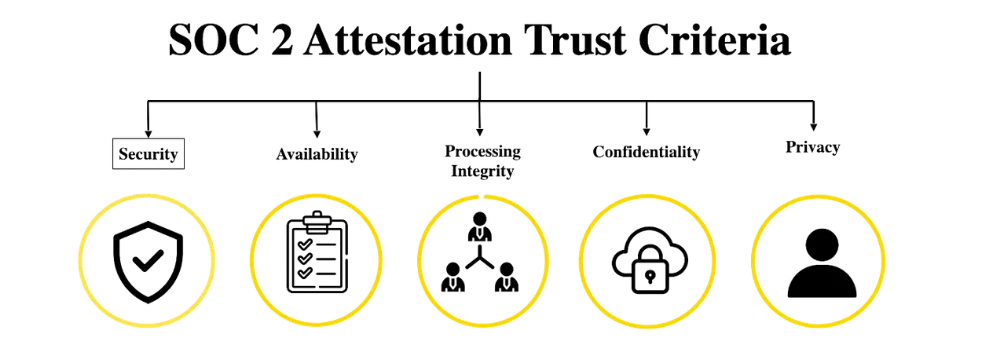
SOC 2 (System and Organization Controls) is an attestation report developed based on the audit results by the approved organization of American Institute of Certified Public Accountants (AICPA) that evaluates how an organization designs and operates controls to protect customer data and systems. It focuses on internal controls relevant to security, availability, processing integrity, confidentiality, and privacy.
SOC 2 is applicable to service organizations that store, process, or transmit customer data, particularly technology, SaaS, cloud, and IT-enabled service providers
SOC 2 attestation demonstrates an organization’s commitment to safeguarding customer information and maintaining a strong control environment. It provides independent assurance that security and operational controls are appropriately designed and, where applicable, operating effectively to protect customer data and systems.
SOC 2 helps organizations to Establish trust with customers and stakeholders. Demonstrate accountability for data security and system reliability Reduce risks related to data breaches and service disruptions Meet customer, regulatory, and contractual assurance requirements Strengthen governance over information security and operations

SOC 2 assessments are based on one or more of the following Trust Services Criteria, selected by the organization:
SOC 2 Type I
Evaluates the design of controls at a specific point in time. Suitable for first-time SOC assessments. Provides quicker assurance to customers
SOC 2 Type II
Evaluates both design and operating effectiveness of controls. Covers a defined audit period (typically 6–12 months). Provides stronger assurance and is expected annually
By working with a SOC 2 attested organization, clients and partners gain:
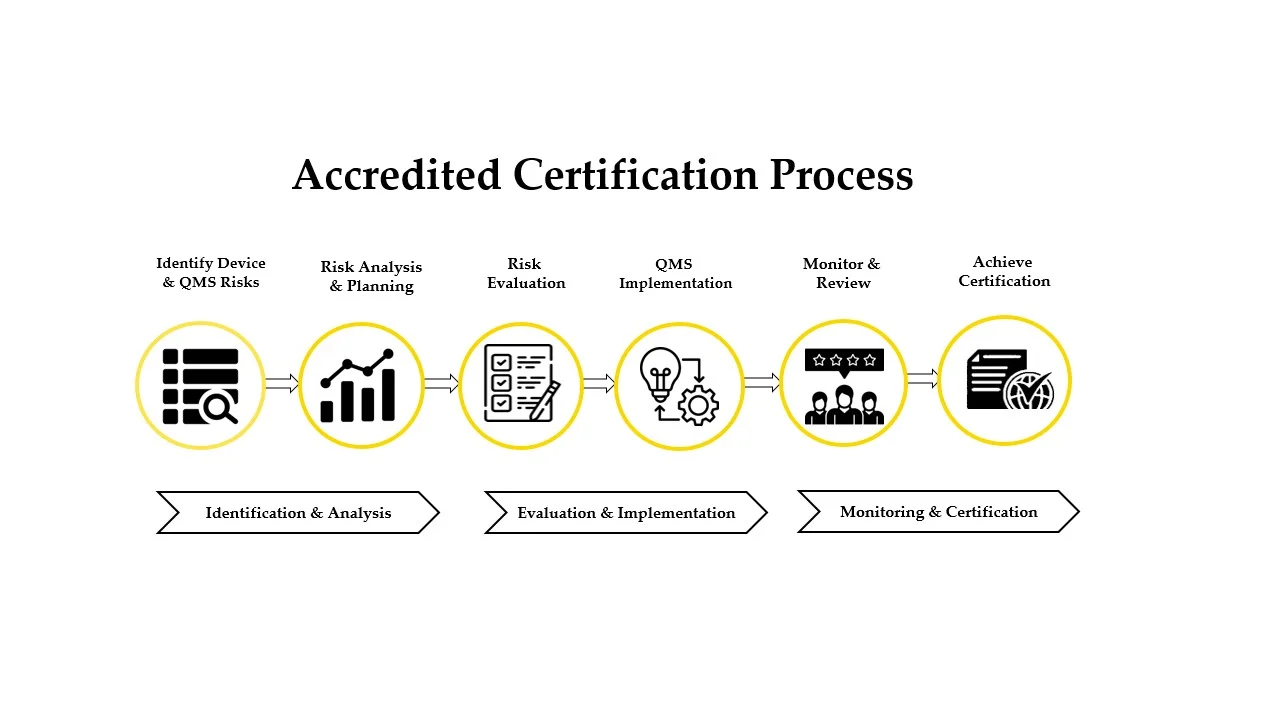
Strengthen credibility, meet international compliance standards, and build trust with customers and stakeholders through globally recognized ISO and compliance certifications.
TESTIMONIALS
Excellent training! The blend of theoretical knowledge and hands-on application elevated my auditing skills. Highly recommended for anyone aspiring to become an ISO 27001 Lead Auditor.